There are different types of protocol in our Industrial automation industry. For Network protocol some internationally defined protocols we use.
Set of rules that two or more devices must follow if they need to communicate with each other. It include most of the things like data, Voltage level etc. Network level defines how a network will handle following problems and task like:
1. Communication line error
2. Flow control
3. Access by multiple devices
4. Failure detection
5. Data translation
6. Interpretation of Messages
Some international protocol standards are :
1. OSI Model
2. IEEE protocol
3. TCP/IP protocol
OSI model : Open system interconnection model (OSI model) is standard protocol based telecommunication model that is accepted internationally. In 1970 there are two network architecture are working, One was administered by the International Organization for Standardization (ISO), while the other was undertaken by the International Telegraph and Telephone Consultative Committee. In 1983 international organization for standardization merged these two international documents in one and called it basic reference model for open system interconnections.
Note: OSI model is not really a protocol. This is model for standardization.
In this model, they introduced 7 layers for different steps of operations. 7 layers are:
Layer 1: Physical Layer
The physical layer has the following major functions:
- It defines the electrical and physical specifications of the data connection. It defines the relationship between a device and a physical transmission medium (e.g., a copper or optical fiber cable, radio frequency). This includes the layout of pins, voltages, line impedance, cable specification, signal timing and similar characteristics for connected devices and wavelength (5 GHz or 2.4 GHz etc) for wireless devices.
- It defines transmission mode i.e. simplex, half duplex, full duplex.
- It defines the network topology as bus, mesh, or ring being some of the most common.
.
Layer 2: Data Link Layer
The Data link layer provides node to node data transfer -- a link between two directly connected nodes. It detects and possibly corrects errors that may occur in the physical layer. It, among other things, defines the protocol to establish and terminate a connection between two physically connected devices. It also defines the protocol for flow control between them.
IEEE802 divides the data link layer into two sublayers:
· Media access control (MAC) layer - responsible for controlling how devices in a network gain access to data and permission to transmit it.
- Logical link control (LLC) layer - responsible for identifying Network layer protocols and then encapsulating them and controls error checking and packet synchronization.
The point to point protocol (PPP) is a data link layer that can operate over several different physical layers, such as synchronous and asynchronous serial lines.
The ITU-T G.Hn standard, which provides high-speed local area networking over existing wires (power lines, phone lines and coaxial cables), includes a complete data link layer that provides both error correction and flow control by means of a selective repeat sliding window protocol.
Layer 3: Network Layer
The network layer provides the functional and procedural means of transferring variable length data sequences (called datagram) from one node to another connected to the samenetwork. It translates logical network address into physical machine address. A network is a medium to which many nodes can be connected, on which every node has anaddress and which permits nodes connected to it to transfer messages to other nodes connected to it by merely providing the content of a message and the address of the destination node and letting the network find the way to deliver ("route") the message to the destination node. In addition to message routing, the network may (or may not) implement message delivery by splitting the message into several fragments, delivering each fragment by a separate route and reassembling the fragments, report delivery errors, etc.
Datagram delivery at the network layer is not guaranteed to be reliable.
A number of layer-management protocols, a function defined in the management annex, ISO 7498/4, belong to the network layer. These include routing protocols, multicast group management, network-layer information and error, and network-layer address assignment. It is the function of the payload that makes these belong to the network layer, not the protocol that carries them.
Layer 4: Transport Layer
The transport layer provides the functional and procedural means of transferring variable-length data sequences from a source to a destination host via one or more networks, while maintaining the quality of service functions.
An example of a transport-layer protocol in the standard Internet stack is transmission control protocol (TCP), usually built on top of the internet protocol (IP).
The transport layer controls the reliability of a given link through flow control, segmentation/ desegmentation, and error control. Some protocols are state and connection-oriented. This means that the transport layer can keep track of the segments and retransmit those that fail. The transport layer also provides the acknowledgement of the successful data transmission and sends the next data if no errors occurred. The transport layer creates packets out of the message received from the application layer. Packetizing is a process of dividing the long message into smaller messages.
Layer 5: Session Layer
The session ;ayer controls the dialogues (connections) between computers. It establishes, manages and terminates the connections between the local and remote application. It provides for Full duplex, half duplex or simplex operation, and establishes check pointing, adjournment, termination, and restart procedures. The OSI model made this layer responsible for graceful close of sessions, which is a property of the transmission control protocol, and also for session check pointing and recovery, which is not usually used in the Internet Protocol Suite. The session layer is commonly implemented explicitly in application environments that use remote procedure calls.Layer 6: Presentation Layer
The presentation layer establishes context between application-layer entities, in which the application-layer entities may use different syntax and semantics if the presentation service provides a big mapping between them. If a mapping is available, presentation service data units are encapsulated into session protocol data units, and passed down the protocol stack.This layer provides independence from data representation (e.g., encryption) by translating between application and network formats. The presentation layer transforms data into the form that the application accepts. This layer formats and encrypts data to be sent across a network. It is sometimes called the syntax layer.
Layer 7: Application Layer
The application layer is the OSI layer closest to the end user, which means both the OSI application layer and the user interact directly with the software application. This layer interacts with software applications that implement a communicating component. Such application programs fall outside the scope of the OSI model. Application-layer functions typically include identifying communication partners, determining resource availability, and synchronizing communication. When identifying communication partners, the application layer determines the identity and availability of communication partners for an application with data to transmit. When determining resource availability, the application layer must decide whether sufficient network or the requested communication exists. In synchronizing communication, all communication between applications requires cooperation that is managed by the application layer. This layer supports application and end-user processes. Communication partners are identified, quality of service is identified, user authentication and privacy are considered, and any constraints on data syntax are identified. Everything at this layer is application-specific.(Note: Description of OSI model is taken from Wikipedia.)
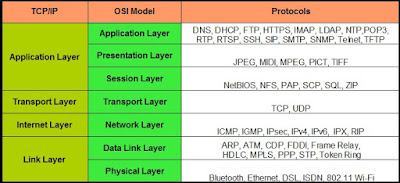
TCP/ IP protocol: Transmission control protocol/ Internet protocol is standard protocol followed by all over the world and is based on OSI model. This protocol is shorten into five layers only and those are:
1. Physical layer
2. Data link layer
3. Internet protocol
4. Transmission control protocol/ User datagram protocol
5. Application protocol
There are five layers as shown below on the reference of OSI model.
Now it is important that which type of prtocol and services are provided by different layers. The below figure suggests the protocol and services used in OSI as well as in TCP/IP protocol. At the time of intoduction of TCP/IP, it has five layers but later on Physical and Data link is taken as one layer and it is named as Network interface layer.
We also have difference in protocol system. OSI model is different from TCP/IP as shown below.







No comments:
Post a Comment